CCSP: IT Security Evaluations and Common Criteria (CC)
Common Criteria (CC), Evaluation Assurance Levels, IT Security Evaluations
What is an IT Security Evaluation?
IT security evaluation is
The process of systematically examining an organisation’s IT systems and infrastructure to identify and assess security vulnerabilities and risks.
IT security evaluation helps organisations:
Understand their security posture
Identify potential weaknesses
Prioritise remediation efforts
Types of IT security evaluations
Vulnerability scanning: Identifies known vulnerabilities in software, hardware, and network configurations.
Penetration testing: Simulates real-world cyberattacks to identify exploitable vulnerabilities and assess their impact.
Security audits: Reviews security policies, procedures, and controls to ensure they are adequate and effective.
Risk assessments: Evaluates the likelihood and potential impact of security threats to the organisation.
Benefits of IT security evaluation
IT security evaluation is crucial for multiple reasons that impact various aspects of an organisation’s operations and security posture.
Identify vulnerabilities and weaknesses: It acts as a proactive measure to identify potential vulnerabilities and weaknesses in your IT systems and infrastructure before they can be exploited by attackers. This allows organisations to prioritise remediation efforts and address critical issues first.
Improve security posture: By identifying and addressing vulnerabilities, organisations can significantly improve their overall security posture, making them less susceptible to cyberattacks. This can lead to reduced risk of data breaches, financial losses, and reputational damage.
Meet compliance requirements: Many industries and regulations have specific security requirements that organisations must comply with. IT security evaluations can help organisations demonstrate compliance with these regulations, avoiding potential fines and penalties.
Inform security decisions: The findings from an IT security evaluation can provide valuable insights that can inform future security decisions and investments. This can help organisations allocate resources more effectively and focus on the most critical security needs.
Increase visibility and awareness: IT security evaluations can help raise awareness of security risks within an organisation. This can lead to a more security-conscious culture and encourage employees to take steps to protect their data and systems.
Reduce long-term costs: Proactive identification and mitigation of vulnerabilities can prevent costly security incidents in the long run. This can save organisations money in terms of
data breach response,
remediation efforts, and
legal fees.
Common Evaluation Frameworks
Frameworks provide a structured and standardised approach to conducting security evaluations.
Many frameworks are aligned with industry regulations and standards, making compliance easier to achieve.
Frameworks ensure that an organisation has a clear roadmap for meeting its compliance obligations.
Common Criteria: An international standard for evaluating the security of IT products and systems.
FedRAMP: A US government framework for assessing the security of cloud services.
FIPS 140-2: A US standard for evaluating the security of cryptographic modules.
NIST Cybersecurity Framework: A voluntary framework for managing cybersecurity risk.
Common Criteria (CC)
Governments and agencies require technology partners and suppliers to obtain certain IT security evaluation certifications for several critical reasons.
Increase trust and confidence: Certifications demonstrate that a supplier’s technology has undergone rigorous independent testing and meets specific security standards. This provides governments and agencies with greater trust and confidence in the supplier’s ability to protect sensitive data and systems.
Reduced risk of security breaches: By requiring certified technology, governments and agencies can significantly reduce the risk of security breaches and cyberattacks. This protects
Critical infrastructure
Sensitive information
National security interests
Enhanced transparency and accountability: Certifications offer a standardised way to measure and compare the security posture of different technology vendors. Certifications
Promote supply chain transparency and accountability.
Helps governments/agencies make informed procurement decisions.
Compliance with regulations and laws: Many governments and agencies are subject to strict regulations and laws that require them to use technology that meets specific standards. Obtaining relevant certifications helps suppliers
Demonstrate compliance.
Avoid potential legal repercussions.
Improved interoperability and collaboration: By requiring technology certified under common standards, governments/agencies can ensure interoperability between different systems and platforms. This facilitates collaboration and improves overall security posture.
Level playing field for suppliers: Certifications create a level playing field for technology suppliers by ensuring that all vendors meet the same minimum security requirements. This promotes fair competition and prevents unfair advantage for specific suppliers.
Promote innovation and best practices: To meet ever-evolving threats, certification requirements encourage technology suppliers to
Invest in security R&D.
Adopt best practices.
Common Criteria (CC) is an international standard for evaluating the security of IT products and systems.
It provides a rigorous framework for assessing and verifying the security claims of IT products, allowing users to make informed decisions about their security investments.
It aims to address the need for a standardised approach to IT security evaluation, overcoming the limitations of individual national schemes.
It promotes harmonisation and mutual recognition of evaluation results across different countries.
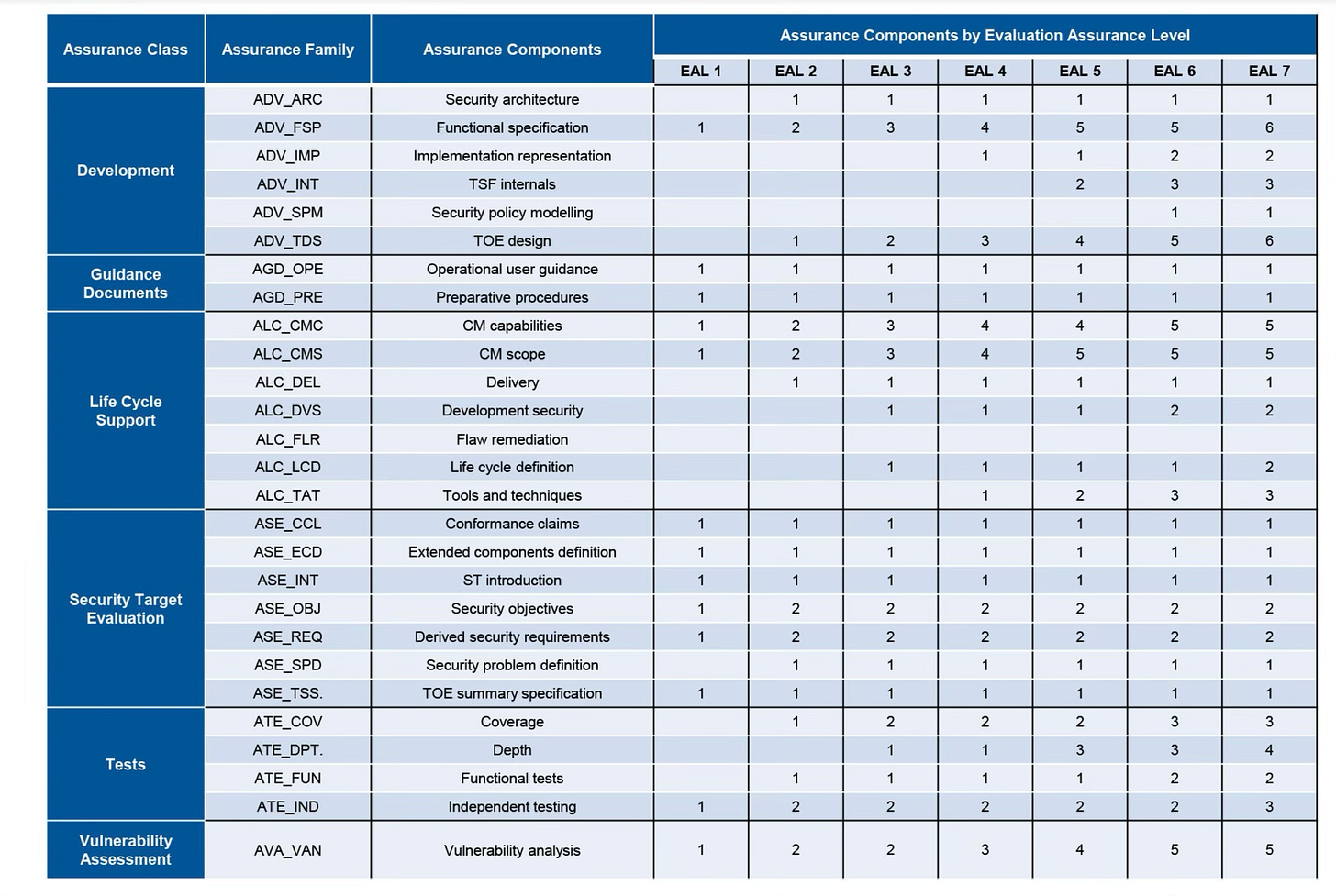
Common Criteria - Components
Enterprise Assurance Levels: Define the depth and rigour (thoroughness) of the security evaluation. The levels range from EAL1 (basic) to EAL7 (rigorous).
Protection profiles (PPs): Protection profiles define the specific security requirements for a particular type of product or system, such as a smart card or operating systems.
Security Target (ST): Security target (ST) is a document provided by the technology vendor or manufacturer that specifies (what it seeks to comply with) the
Security objectives
Claims
EAL
PP
Common Methodology for Information Technology Security Evaluation (CEM): Is the technical basis for conducting common criteria evaluations. It provides a set of guidelines and procedures for evaluators.
Security claim: A security claim is a statement made by a product developer or vendor about the security properties and capabilities of their product. Claims are typically documented in a security target (ST), which is a key component of the CC evaluation process.
Functional claims: Functional claims specify what the product is supposed to do in terms of security, such as protecting confidentiality, integrity, and availability.
Assurance claims: Assurance claims address the level of confidence that can be placed in the security claims, based on the evaluation conducted according to the chosen EAL.
Operational claims: Operational claims describe the security features and mechanisms that the product uses to achieve its security objectives.
Environmental claims: Environmental claims specify the conditions under which the product is expected to function securely.
Enterprise Assurance Levels (EALs)
EAL 1 - Functionally Tested
It confirms basic functionality and states that the product meets the stated security objectives.
It provides limited testing and analysis of the documentation provided by the product developer.
It is suitable for low-risk applications where security is not critical.
EAL 2 - Structurally Tested
It verifies the internal structure of the product and confirms it adheres to design specifications.
It provides
Extensive functional testing.
Code review.
Analysis of the product documentation provided by the product developer.
It is suitable for moderate-risk applications where some security assurance is desired.
EAL3 - Methodically Tested and Checked
It focuses on the assessment of the development process and ensures systematic testing and analysis.
It provides
Rigorous functional/ configuration testing.
Vulnerability analysis.
Evaluation of development procedures.
It is suitable for high-risk applications where strong security guarantees are needed.
EAL4 - Methodically Designed, Tested, and Reviewed
It evaluates the design and development process to ensure it incorporates security best practices.
It provides
Extensive security testing.
Penetration testing.
Formal design review.
It is suitable for highly sensitive applications where the highest levels of assurance are required.
EAL5 - Semi-Formally Designed and Tested
It assesses the design and development process using formal methods and tools.
It provides
Formal verification of security properties
Rigorous penetration testing.
Independent security audit.
It is suitable for mission-critical applications where the security is unassailable (unable to be attacked, defeated).
EAL6 - Semi-Formally Verified Design and Tested
Employs formal methods to verify the security design and thoroughly tests the implementation.
It provides
Extensive formal verification.
Penetration testing.
Independent security audit with formal analysis methods.
It is suitable for highly sensitive systems with extremely high security requirements.
EAL7 - Formally Verified Design and Tested
Uses formal methods to rigorously verify both the design and implementation of the product.
It provides
Extensive formal verification and proof of correctness.
Rigorous penetration testing.
Independent security audit with formal analysis methods.
It is suitable for life-critical systems where the failure of security could have catastrophic consequences.
Key Takeaways
Higher EAL levels offer more assurance but require more resources and time to achieve.
The appropriate EAL level depends on the intended use of the product and the associated risk profile.
EALs are a valuable tool for organisations seeking to understand and compare the security of IT products and systems.
It should be noted that a level 7 product, for example, is not automatically more secure than a level 5 product. The level 7 product has simply undergone more testing.